About
A service principal name is a principal for a service
Service Class/<host name>
where:
- The service-class is a string and identifies the general class of service. Computers or machine accounts automatically get an SPN with a service class of “host.” Other well-known service class names are:
- “www” for a Web service
- “ldap” for a directory service.
- “HTTP” for configuring SPNEGO for browser-based SSO. The HTTP service class differs from the HTTP protocol: both the HTTP protocol and the HTTPS protocol use the HTTP service class.
Generally, the service class name can be any string that is unique to the service class
An SPN (Service Principal Name) is a unique name that identifies an instance of a service and is associated with the logon account under which the service instance runs.
It provides a mapping between the AD user account and the service instance and allows for the multipart name format used in Kerberos principal names (e.g. HTTP/hostname.dns.com).
The SPN is used in the process of mutual authentication between the client and the server hosting a particular service. The client finds a computer account based on the SPN of the service to which it is trying to connect.
Service Principal Names MUST be unique across the entire (LDAP|Active Directory) forest.
Service Principal Names define what services run under the accounts security context.
Articles Related
Account
Service Principal Names can be assigned to either:
- User accounts (Service Account)
- or Computer accounts.
Service Accounts
Service Principal Names can be defined on user accounts when a Service or application is running under that users Security context. Typically these types of user accounts are known as “Service Accounts”. It is very import that you understand that Service Principal Names MUST be unique throughout the entire Active Directory forest.
Some typical scenarios when a user account has a Service Principal Name defined are:
- When SQL Server Service is using a user account or “Service Account” instead of the default of “LocalSystem”. An example is: MSSQLSvc/sqlsrvr.contoso.com:1433
- When an IIS Web Application Pool is running as a specified user account rather than as the default of “Network Service”. An example is: http/websrvr.contoso.com
- the service invoked by the WebLogic browser clients is HTTP/myhost.example.com, which needs to be linked to the myhost account.
LDAP
Windows
Windows account names are not multipart as Kerberos principal names. Because of this, it is not possible to directly create an account using the name HTTP/hostname.dns.com. Such a principal instance is created through service principal name mappings. In this case, an account is created with a meaningful name hostname, and a service principal name mapping is added for HTTP/hostname.dns.com.
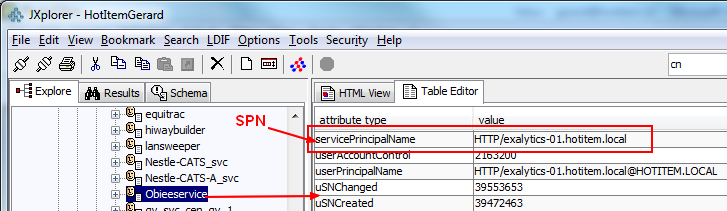
The SPN of an Active Directory object is an attribute of the object, and can only hold a single value.
The attribute name is servicePrincipalName.
Management
Create
Use the setspn command to map the Kerberos service principal name, HTTP/
, to a Microsoft user account. An example of setspn usage is as follows:
C:\Program Files\Support Tools>
setspn -A HTTP/myHost.gerardnico.com myHost
where:
- myHost is a Microsoft user account
- and HTTP/myHost.gerardnico.com is a SPN
Utilties
- LDP, LDIFDE (to query LDAP for all objects that have the SPN defined on them.),
- ADSIEdit, or SetSPN. (to see what SPNs are registered on a given object)
setspn -L
You can also see them with the Mit Klist
klist
Ticket cache: API:Initial default ccache
Default principal: gerardn@REALM
Valid starting Expires Service principal
07/26/18 10:57:05 07/26/18 20:57:05 krbtgt/REALM@REALM
renew until 08/02/18 07:57:05
07/26/18 10:57:05 07/26/18 20:57:05 hive/FQhostName@REALM
renew until 08/02/18 07:57:05