Cyrptography - Certificate chain
About
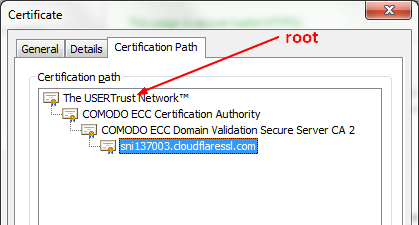
A certificate can have been issued (signed) by another CA creating a chain (or path). See certificate chain
There are several types of certificate:
- root certificate. The root of the tree. (All root CA certificates are self signed)
- intermediate certificate. The beginning of a branch of the tree (signed by the root)
- the certificate. The leaf of the tree signed by the intermediate.
Management
See
- from the chrome dev tool (F12) > security.
- Direct issuer (first level)
openssl x509 -noout -subject -issuer -in file.pem
subject= /CN=server01.bytle.net
issuer= /C=US/O=Let's Encrypt/CN=Let's Encrypt Authority X3
Length
- with Cryptography - Keytool (Key and Certificate Management Tool) and the -v option
keytool -list -v -storetype jks -keystore truststore.jks -storepass changeit
...
Certificate chain length: 1
...
Show remotely
The shows the chain from the root to the leaf
Example:
openssl s_client -connect gerardnico.com:443 -servername gerardnico.com -showcerts -prexit
- Certificate chain verification
Loading 'screen' into random state - done
CONNECTED(000001A4)
depth=3 C = SE, O = AddTrust AB, OU = AddTrust External TTP Network, CN = AddTrust External CA Root
verify return:1
depth=2 C = GB, ST = Greater Manchester, L = Salford, O = COMODO CA Limited, CN = COMODO ECC Certification Authority
verify return:1
depth=1 C = GB, ST = Greater Manchester, L = Salford, O = COMODO CA Limited, CN = COMODO ECC Domain Validation Secure Server CA 2
verify return:1
depth=0 OU = Domain Control Validated, OU = PositiveSSL Multi-Domain, CN = sni137003.cloudflaressl.com
verify return:1
Check / verify
See Certificate and chain verification