About
This page shows you yow to configure Postfix to enable remote connections to the Postfix SMTP server on the port 587 (submission port) with authentication.
Postfix used SASL as authentication library and this instructions shows how to set it up with the default authentication mechanism (ie PAM)
As only the submission port should allow authentication, all configuration should not be written in the /etc/postfix/main.cf file but has a command line argument in the /etc/postfix/master.cf below the submission line. We will see that further in the steps.
Once a client is authenticated, a server generally give the “same network” privileges.
Articles Related
SASL
implementations supported
Postfix support the following SASL implementations (ie compiled into Postfix)
# SASL support in the SMTP server
postconf -a
# or SASL support in the SMTP+LMTP client
# postconf -A
cyrus
dovecot
By default the Postfix SMTP server uses the Cyrus SASL implementation.
Cyrus SASL
Communication between Postfix and Cyrus SASL takes place by calling functions in the SASL library (The Postfix SMTP server is linked with the Cyrus SASL library libsasl)
Steps
Cyrus SASL Smtp configuration file
This steps shows just how it works. If you are good with the default mechanism , you don't need to change anything
- The file name is set in a configuration property that depends of the Postfix version
# for postfix >= 2.3
echo The name of the configuration is the $(postconf -h smtpd_sasl_path).conf
# for postfix < 2.3
# echo The name of the configuration is the $(postconf -h smtpd_sasl_application_name).conf
The name of the configuration is the smtpd.conf
- The directory depends of the version and the compilation (generally in /etc/sasl2/ or usr/lib/sasl2 ). The content of the configuration file is:
# Cyrus SASL Version in /etc/sasl2/
cat /etc/sasl2/smtpd.conf
# or /usr/lib/sasl2/smtpd.conf
# list of mechanisms used to verify passwords
pwcheck_method: saslauthd
# Whitespace separated list of mechanisms to allow
mech_list: plain login
# Whitespace separated list of mechanisms to allow
log_level: 7
where:
All Cyrus SASL configuration are described in this page: Options for Cyrus SASL
- the SASL password check mechanism used is the saslauthd mechanism that used itself by default PAM as backend. See SASL - saslauthd server (Cyrus SASL)
- Plaintext mechanisms (PLAIN, LOGIN) send credentials unencrypted. This information should be protected by an additional security layer such as a TLS-encrypted SMTP session
Posfix conf
In the master file, uncomment the submission
submission inet n - n - - smtpd
-o syslog_name=postfix/submission
-o smtpd_tls_security_level=encrypt
-o smtpd_sasl_auth_enable=yes
-o smtpd_reject_unlisted_recipient=no
-o smtpd_client_restrictions=$mua_client_restrictions
-o smtpd_helo_restrictions=$mua_helo_restrictions
-o smtpd_sender_restrictions=$mua_sender_restrictions
-o smtpd_recipient_restrictions=permit_sasl_authenticated,reject
-o milter_macro_daemon_name=ORIGINATING
Ssl must be already configured to support smtpd_tls_security_level=encrypt) in order to encrypt the password in transit (otherwise they are send in clear).
See this article that shows how to do it: How to configure Postfix for TLS / SSL and StartTLS?
Services
SASL server and mechanism
- Be sure that saslauthd is on
systemctl status saslauthd
# if not
# systemctl start saslauthd
saslauthd.service - SASL authentication daemon.
Loaded: loaded (/usr/lib/systemd/system/saslauthd.service; enabled; vendor preset: disabled)
Active: active (running) since Sat 2020-06-20 14:14:57 CEST; 5min ago
Process: 26967 ExecStart=/usr/sbin/saslauthd -m $SOCKETDIR -a $MECH $FLAGS (code=exited, status=0/SUCCESS)
Main PID: 26968 (saslauthd)
- Install the plain text SASL mechanism
yum install cyrus-sasl-plain
Postfix
- Restart postfix
systemctl restart postfix
systemctl status postfix
postfix.service - Postfix Mail Transport Agent
Loaded: loaded (/usr/lib/systemd/system/postfix.service; enabled; vendor preset: disabled)
Active: active (running) since Sat 2020-06-20 14:15:00 CEST; 4min 16s ago
Process: 26999 ExecStop=/usr/sbin/postfix stop (code=exited, status=0/SUCCESS)
Process: 27014 ExecStart=/usr/sbin/postfix start (code=exited, status=0/SUCCESS)
Process: 27012 ExecStartPre=/usr/libexec/postfix/chroot-update (code=exited, status=0/SUCCESS)
Process: 27010 ExecStartPre=/usr/libexec/postfix/aliasesdb (code=exited, status=0/SUCCESS)
Main PID: 27087 (master)
Tasks: 6
Memory: 6.4M
CGroup: /system.slice/postfix.service
├─27087 /usr/libexec/postfix/master -w
├─27088 pickup -l -t unix -u
├─27089 qmgr -l -t unix -u
├─27093 showq -t unix -u
├─27120 tlsmgr -l -t unix -u
└─27121 anvil -l -t unix -u
Test
Port 587 bound
Verify that the port is now bound to the master process with netstat
netstat -tulpn | { read header; read header2; echo $header; echo $header2; grep master; }
- Below we can see that the port 587 and 25 are bound to the master process
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN 27087/master
tcp 0 0 0.0.0.0:587 0.0.0.0:* LISTEN 27087/master
tcp6 0 0 :::25 :::* LISTEN 27087/master
tcp6 0 0 :::587 :::* LISTEN 27087/master
saslauthd test
Test the configuration of saslauthd to see if you can connect
testsaslauthd -u username -p password -s smtp
0: OK "Success."
SMTP authentication
testing with SMTP command
- connect to your server with openssl
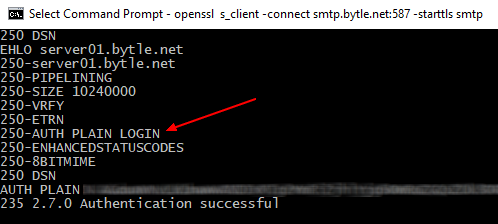
openssl s_client -connect server:587 -starttls smtp
250 DSN
EHLO server
250-server
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-AUTH PLAIN LOGIN # The auth is advertised
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
- In another console (terminal), compute the authentication string (It's just a base64 string with name and password)
printf '\0%s\0%s' 'user' 'pwd' | openssl base64
AHVzZXIAcHdk
- Authenticate
AUTH PLAIN TheBase64String
# example
# AUTH PLAIN AHVzZXIAcHdk
235 2.7.0 Authentication successful
Log
When making a connection with openssl, you should see a log that looks like that:
tail -f /var/log/maillog
Jun 20 21:03:33 server01 postfix/submission/smtpd[13032]: connect from unknown[x.x.x.x]
Jun 20 21:03:33 server01 postfix/submission/smtpd[13032]: Anonymous TLS connection established from unknown[x.x.x.x]: TLSv1.2 with cipher ECDHE-RSA-AES256-GCM-SHA384 (256/256 bits)
Jun 20 21:03:43 server01 postfix/submission/smtpd[13032]: lost connection after UNKNOWN from unknown[x.x.x.x]
Jun 20 21:03:43 server01 postfix/submission/smtpd[13032]: disconnect from unknown[143.176.206.82]
Jun 20 21:03:53 server01 postfix/submission/smtpd[13032]: connect from unknown[143.176.206.82]
Jun 20 21:03:54 server01 postfix/submission/smtpd[13032]: Anonymous TLS connection established from unknown[x.x.x.x]: TLSv1.2 with cipher ECDHE-RSA-AES256-GCM-SHA384 (256/256 bits)
Jun 20 21:11:05 server01 postfix/submission/smtpd[13032]: lost connection after AUTH from unknown[x.x.x.x]
Jun 20 21:11:05 server01 postfix/submission/smtpd[13032]: disconnect from unknown[x.x.x.x]