About
Transport Layer Security (TLS, formerly called SSL) with Postfix
It provides:
- and encrypted sessions.
An encrypted session protects the information that is transmitted:
- with SMTP mail (ie mail encryption)
- or with SASL authentication. (ie login encryption)
TLS is based on OpenSSL
Steps
Certificate and private key
Format
In order to use TLS, the Postfix SMTP server needs a certificate and a private key.
- Both must be in “PEM” format.
- The private key must not be encrypted, meaning: the key must be accessible without a password.
- If the key is stored:
- in the same file with the certificate, this should be owned by “root” and not be readable by any other user.
- in a separate file:
- the private should be owned by “root” and not be readable by any other user.
- the certificate file may be “world-readable”.
You can create them with certbot
For instance if you use OVH as your domain provider, you could ask a certificate like that:
certbot certonly \
--dns-ovh \
--dns-ovh-credentials /root/.secrets/certbot/ovh.ini \
--dns-ovh-propagation-seconds 60 \
-n \
--agree-tos \
-m your_email \
-d your.server.name # for instace server01.example.com
Verification
The Postfix SMTP server certificate must be usable as SSL server certificate and hence pass the verify test:
# example
cd /etc/letsencrypt/live/<your.server>/
openssl verify -untrusted chain.pem -verbose -purpose sslserver fullchain.pem
fullchain.pem: OK
To know more about this command, see Check a certificate and its intermediate certificate chain.
Configuration
- Certificate and private key postconf.5.html and postconf.5.html
smtpd_tls_cert_file = /etc/letsencrypt/live/<your.server>/fullchain.pem
smtpd_tls_key_file = /etc/letsencrypt/live/<your.server>/privkey.pem
Trusted CA
To verify a remote SMTP client certificate, the Postfix SMTP server needs to trust the certificates of the issuing Certification Authorities.
Optional as the CA authorities are normally already installed.
Centos
You can verify that the CA are already installed in the certs directory
ls /etc/ssl/certs/*.crt
/etc/ssl/certs/ca-bundle.crt /etc/ssl/certs/ca-bundle.trust.crt
On Centos the package ca-certificates is responsible to update them
yum info ca-certificates
Installed Packages
Name : ca-certificates
Arch : noarch
Version : 2019.2.32
Release : 76.el7_7
Size : 968 k
Repo : installed
From repo : updates
Summary : The Mozilla CA root certificate bundle
URL : http://www.mozilla.org/
License : Public Domain
Description : This package contains the set of CA certificates chosen by the
: Mozilla Foundation for use with the Internet PKI.
Configuration
If you want to specify them you can specify them (in PEM Format) via the following configuration:
- postconf.5.html: a single file with all CA in a pem format
- postconf.5.html: one CA per file in the directory. Don't forget to create the necessary “hash” links with:
$OPENSSL_HOME/bin/c_rehash /path/to/directory
Configuration
Smtp Server
The smtpd_tls configuration (receiving side) for all postfix process
- postconf.5.html: Security level for the Postfix SMTP server. may because according to search/rfc_search_detail.php, ecnrypt MUST NOT be applied in case of a publicly-referenced SMTP server. On the submission port (587), you should override this value to encrypt
smtpd_tls_security_level = may
- postconf.5.html: 1 = Log only a summary message on TLS handshake completion
smtpd_tls_loglevel = 1
- postconf.5.html: Request that the Postfix SMTP server produces Received: message headers that include information about the protocol and cipher used
smtpd_tls_received_header = yes
Smtp Client
The smtp_tls configurations (sending side)
- postconf.5.html: Security level for the Postfix SMTP client
smtp_tls_security_level = encrypt
- postconf.5.html: Log the hostname of a remote SMTP server that offers STARTTLS, when TLS is not already enabled for that server.
smtp_tls_note_starttls_offer = yes
Test
Gmail
Send an email
echo "Body: This is a test mail. Hallo Charlie" | mail -s "Subject: A big test" [email protected]
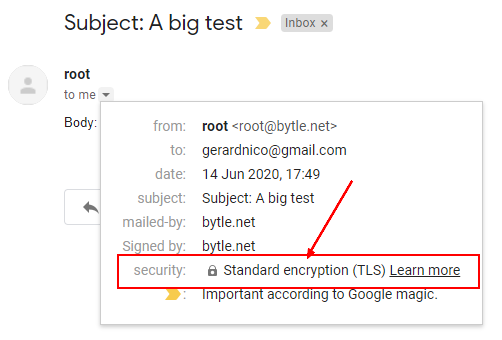
- Check that you got a grey key
- In the original mail, you can see the TLS data
Received: from server01.bytle.net (server01.bytle.net. [164.132.99.202])
by mx.google.com with ESMTPS id k12si12202871wrq.512.2020.06.14.08.49.36
for <[email protected]>
(version=TLS1_2 cipher=ECDHE-ECDSA-AES128-GCM-SHA256 bits=128/128);
Sun, 14 Jun 2020 08:49:36 -0700 (PDT)
Connection to the SMTP server
- A connection to the SMTP server should advertise for STARTTLS
openssl s_client -connect localhost:25 -starttls smtp
- In the log
Jun 14 18:39:27 vps748761 postfix/smtpd[31959]: Anonymous TLS connection established from localhost[127.0.0.1]: TLSv1.2 with cipher ECDHE-RSA-AES256-GCM-SHA384 (256/256 bits)
You may or you may not be able to send an email via an Anonymous TLS connection through a port connection.
STARTTLS Command
The STARTTLS keyword in response to the HELO command advertises that the server supports STARTTLS and that the client can issue a STARTTLS command to secure the connection.
Example:
nc localhost 25
- We receive the banner
220 server01.bytle.net ESMTP Postfix
- HELLO
EHLO server01.bytle.net
- STARTTLS is advertised
250-server01.bytle.net
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-STARTTLS
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
- The client can send the StartTLS command
STARTTLS
- The server responds when it is ready for the handshake.
220 Go ahead
- The client and the servers performs a handshake.
Support
Debug
See postconf.5.html
warning: TLS library problem: 31735:error:140760FC:SSL routines:SSL23_GET_CLIENT_HELLO:unknown protocol:s23_srvr.c:640
You cannot use telnet because it does not support TLS