About
Security regroups many subject area.
The most known are:
- Identity management with:
- authentication (user/password) and its method (ldap, table, …)
- authorization (group, privileges and role, object and information access)
- Crypto with:
- Code:
- output encoding
- …
-
Provide mechanism rather than policy. In particular, place user interface policy in the clients hands
Illustrations
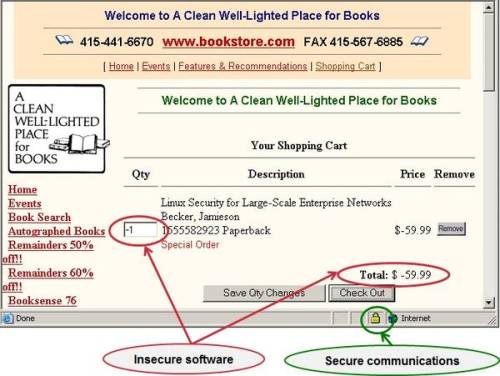
The most effective picture to explain software security.
Everything I try to teach my freshman about security, in one photo:
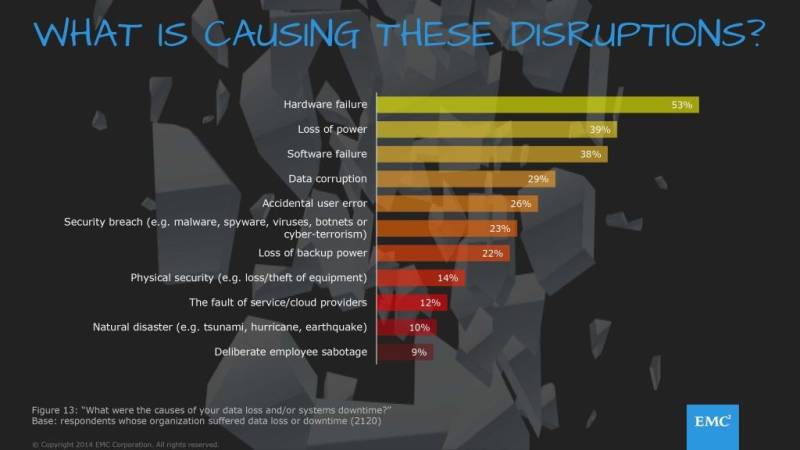
Data Lost
Data Lost or downtime. http://www.emc.com/microsites/emc-global-data-protection-index/index.htm
First Rule
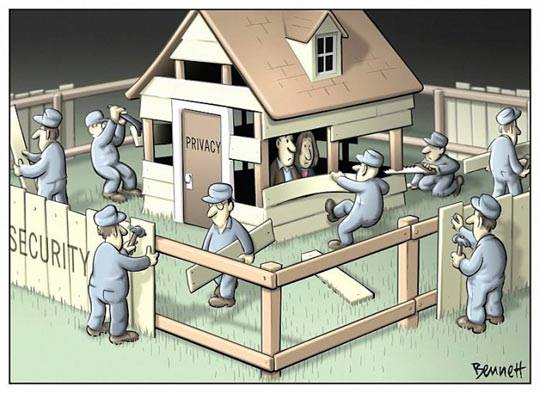
Security / Privacy
En Twitter
Security and bug
The security industry is largely obsessed by finding (and selling / using / patching / reporting / showcasing / stockpiling / detecting / stealing) these “dangerous/useful” variety of bugs. And this obsession is continually fulfilled because bugs keep happening – which is just the nature of software development –
…………