Windows - Firewall
About
Network - Firewall in Windows
Articles Related
Default
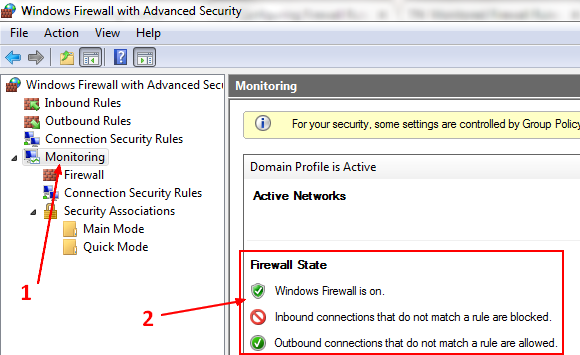
Windows has a built-in firewall that blocks inbound connections.
Profile
netsh advfirewall show currentprofile
Domain Profile Settings:
----------------------------------------------------------------------
State ON
Firewall Policy BlockInbound,AllowOutbound
LocalFirewallRules N/A (GPO-store only)
LocalConSecRules N/A (GPO-store only)
InboundUserNotification Enable
RemoteManagement Disable
UnicastResponseToMulticast Enable
Logging:
LogAllowedConnections Disable
LogDroppedConnections Disable
FileName %systemroot%\system32\LogFiles\Firewall\pfirewall.log
MaxFileSize 4096
Ok.
Local Rule Applied
One liner to get the config for all profiles with Windows - netsh (Netshell)
netsh advfirewall monitor show firewall
Public Profile Settings:
----------------------------------------------------------------------
State ON
Firewall Policy BlockInbound,AllowOutbound
LocalFirewallRules Enable
LocalConSecRules Enable
InboundUserNotification Enable
RemoteManagement Disable
UnicastResponseToMulticast Enable
Logging:
LogAllowedConnections Disable
LogDroppedConnections Disable
FileName %systemroot%\system32\LogFiles\Firewall\pfirewall.log
MaxFileSize 4096
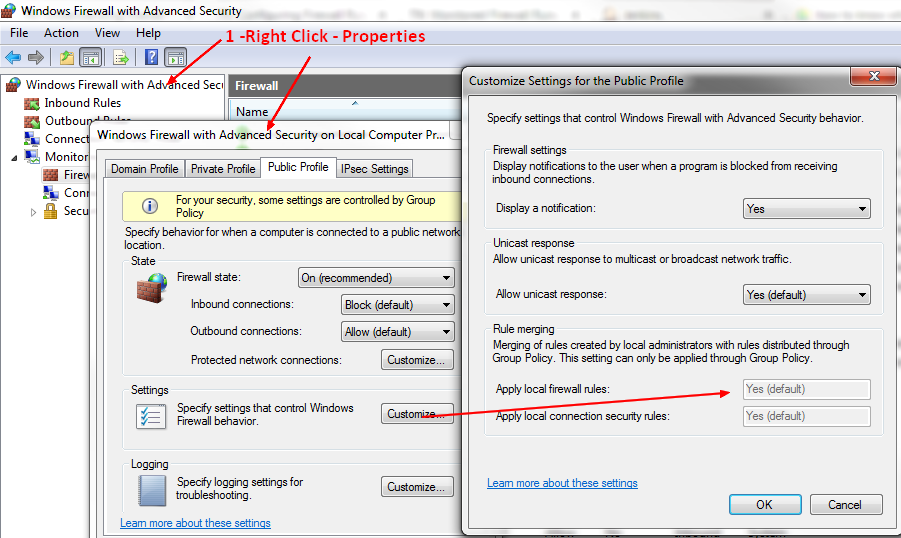
Rules Properties
Configuration Properties for a rule
- inbound traffic or outbound traffic.
- the computers or users, program, service, or port and protocol.
- type of network adapter (local area network (LAN), wireless, remote access, such as a virtual private network (VPN) connection, or all types)
- Profile (used or not) - Domain, Private, Public
Outbound vs Inbound
- outbound: network traffic originating from the computer
- inbound: network traffic originating from the outside: If you want to run a Web server, then you must create an inbound rule that allows unsolicited inbound network traffic on TCP port 80.
Profile
netsh advfirewall monitor show currentprofile
Domain Profile:
----------------------------------------------------------------------
HotITem.local
Ok.
Order of precedence (Priority)
As soon as a network packet matches a rule, that rule is applied, and processing stops.
- 1 - Authenticated bypass. These are rules in which the Override block rules option is selected. These rules allow matching network traffic that would otherwise be blocked. The network traffic must be authenticated by using a separate connection security rule. You can use these rules to permit access to the computer to authorized network administrators and authorized network troubleshooting devices.
- 2 - Block connection. These rules block all matching inbound network traffic.
- 3 - Allow connection. These rules allow matching inbound network traffic. Because the default behavior is to block unsolicited inbound network traffic, you must create an allow rule to support any network program or service that must be able to accept inbound connections.
- 4 - Default profile behavior. The default behavior is to block unsolicited inbound network traffic, but to allow all outbound network traffic. You can change the default behavior on the Domain Profile, Private Profile, and Public Profile tabs of the Windows Firewall with Advanced Security Properties dialog box.
Utility
netsh advfirewall ... # where advfirewall is the context
- Windows Firewall with Advanced Security (wf.msc)
Rules Procedure for a Web Server
- Create your rule ( for instance inbound TCP port 80 ) then
- Restart the computer !