Identification Material - Certificate (or Public Key Certificate)
About
A certificate is a document which permits to define with certainty the owner of the private key (ensures that the party you are communicating with is whom you think.) because it's digitally signed
A certificate may also be known as public key certificate because it uses the public key encryption scheme.
Technically, it is a digitally signed statement that binds the value of a public key to the identity of the person, device, or service that holds the corresponding private key.
The certificate has no role in the encryption. It's a signed document (by a trusted Certificate Authority (CA)) which, ensures that the party you are communicating with is whom you think (A sort of ID card)
When you go to a site that uses HTTPS (connection security), the website's server uses a certificate to prove the website's identity to browsers, like Chrome.
Usage
What are the possible usages of a cryptographic certificate?
Structure
A certificate contains:
- the subject: the certificate itself, ie the owner identification through LDAP attribute (such as names, addresses, and similar identifiers)
- the signature
- the signature algorithm: the algorithm used to sign
- the dates of certificate known as the validity_period
- the public key
- a hash (known as fingerprint) to ensure that the certificate has not been tampered with.
- a list of attributes known as X509v3 extensions
Certificates most commonly comes as .cer file which is added into a keyStore or trustStore by using any key management utility e.g. keytool.
The certificate does and should not contain the private key and can therefore be distributed.
Issuer
The issuer is the entity that signed the certificate through LDAP attribute (such as names, addresses, and similar identifiers).
Serial Number
The serial number 1) is the unique certificate identifier for the CA used during each signature.
The the issuer name and serial number identify a unique certificate.
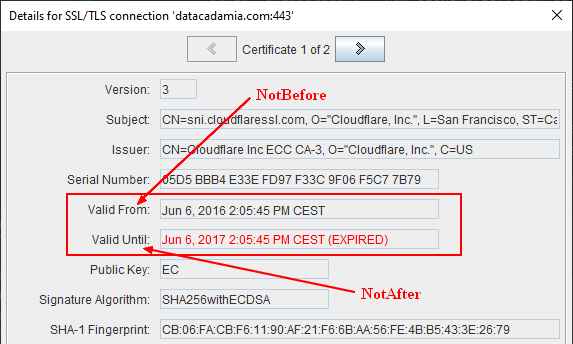
Validity Period
The Validity period is defined 2) as the period of time from notBefore through notAfter, inclusive.
Example with a certificate snapshot from portecle:
Signature
A certificate is insecure until it is signed, as only a signed certificate cannot be modified.
See How a certificate is signed ? (known also as issuing or producing)
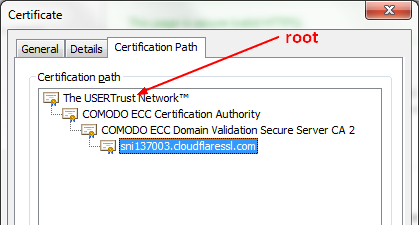
Chain
A certificate can have been signed by another certificate creating a chain (or path)
Generally, it's done by a certificate authority.
The certificate at the top of the chain are called root certificate and are self signed.
Location
This section refers to where the certificate is stored.
Client
A client certificate are used to identify a client or a user, authenticating the client to the server and establishing precisely who they are.
See What is a client certificate authentication ? (SSL/TLS Web)
Server
A server certificate authenticates the server and the owner of the site.
Server certificates typically are issued to:
- hostnames, which could be a machine name (such as WEB-SERVER-01)
- or dns name (such as www.gerardnico.com).
See How to enable SSL on a server (ie HTTPS on a web server) ?
Type
Domain Validated (DV)
Domain Validated certificates are certificates where the domain name is checked against domain registry. They are used to create web server certificate.
Wildcard
A wildcard certificate is a digital certificate that is applied to a domain and all its subdomain.
Example: *.example.com
See also: wiki/Wildcard_certificate
Organization Validated
Organizational certificates are Trusted. Organizations are strictly authenticated by real agents against business registry databases hosted by governments. Documents may exchange and personnel may be contacted during validation to prove the right of use.
OV certificates therefore contain legitimate business information.
This is the standard type of certificate required on a commercial or public facing website. OV certificates conform to the X.509 RFC standards and thus contain all the necessary information to validate the organization.
Details of the certificate (ie Ldap attributes):
Root
Root certificate are the certificate at the root of the chain.
Management
Identifier
The identifier of a certificate is:
- and the serial_number
This concatenation identifies unique a certificate
Format
The format is defined in the x509 specification and the file is generally a pem file with the cer extension
Check
Version
The Version attribute of a certificate gives the X.509 version number.
Installation
The certificate may be installed:
- as on the client side
The Intermediate Certificate Authority Certificates and Certificate Authority Root Certificates need to be added during the installation.
Get
To get a certificate:
Issue
See How a certificate is signed ? (known also as issuing or producing)
Verify
See
How to see a created certificate:
Remote
How to get the server certificate (certificate already installed on the server) ?
Openssl
Openssl where s_client implements a generic SSL client.
openssl s_client -connect localhost:port -servername serverName -showcerts
where
- servname is Server Name Indication (SNI)
- for Azure SQL Server. See Azure SQL server
Example: Output is split in several pieces
openssl s_client -connect gerardnico.com:443 -servername gerardnico.com -showcerts
Loading 'screen' into random state - done
CONNECTED(000001A4)
depth=3 C = SE, O = AddTrust AB, OU = AddTrust External TTP Network, CN = AddTrust External CA Root
verify return:1
depth=2 C = GB, ST = Greater Manchester, L = Salford, O = COMODO CA Limited, CN = COMODO ECC Certification Authority
verify return:1
depth=1 C = GB, ST = Greater Manchester, L = Salford, O = COMODO CA Limited, CN = COMODO ECC Domain Validation Secure Server CA 2
verify return:1
depth=0 OU = Domain Control Validated, OU = PositiveSSL Multi-Domain, CN = sni137003.cloudflaressl.com
verify return:1
where:
- the attributes are ldap attributes:
- depth is the depth in the certificate chain. 0 = leaf - Detail are below in the output.
Certificate chain output
0 s:/OU=Domain Control Validated/OU=PositiveSSL Multi-Domain/CN=sni137003.cloudflaressl.com
i:/C=GB/ST=Greater Manchester/L=Salford/O=COMODO CA Limited/CN=COMODO ECC Domain Validation Secure Server CA 2
-----BEGIN CERTIFICATE-----
MIIHYjCCBwegAwIBAgIRAMktOmOeS7iRAqRtWc9IHD4wCgYIKoZIzj0EAwIwgZIx
CzAJBgNVBAYTAkdCMRswGQYDVQQIExJHcmVhdGVyIE1hbmNoZXN0ZXIxEDAOBgNV
BAcTB1NhbGZvcmQxGjAYBgNVBAoTEUNPTU9ETyBDQSBMaW1pdGVkMTgwNgYDVQQD
Ey9DT01PRE8gRUNDIERvbWFpbiBWYWxpZGF0aW9uIFNlY3VyZSBTZXJ2ZXIgQ0Eg
MjAeFw0xODAyMDEwMDAwMDBaFw0xODA4MTAyMzU5NTlaMGwxITAfBgNVBAsTGERv
bWFpbiBDb250cm9sIFZhbGlkYXRlZDEhMB8GA1UECxMYUG9zaXRpdmVTU0wgTXVs
dGktRG9tYWluMSQwIgYDVQQDExtzbmkxMzcwMDMuY2xvdWRmbGFyZXNzbC5jb20w
WTATBgcqhkjOPQIBBggqhkjOPQMBBwNCAARnBErqfdqoeYpPQqLaDaKC+3lB3+E8
qBW2e7BzyaxoeaLzMxsCJbTVld17CK64OOTTc2VftL6ijsmvnZ0RWvcao4IFYTCC
BV0wHwYDVR0jBBgwFoAUQAlhZ/C8g3FP3hIILG/U1Ct2PZYwHQYDVR0OBBYEFBDT
RmnKk0YMmNRRbt+dVuE0KkJ1MA4GA1UdDwEB/wQEAwIHgDAMBgNVHRMBAf8EAjAA
MB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjBPBgNVHSAESDBGMDoGCysG
AQQBsjEBAgIHMCswKQYIKwYBBQUHAgEWHWh0dHBzOi8vc2VjdXJlLmNvbW9kby5j
b20vQ1BTMAgGBmeBDAECATBWBgNVHR8ETzBNMEugSaBHhkVodHRwOi8vY3JsLmNv
bW9kb2NhNC5jb20vQ09NT0RPRUNDRG9tYWluVmFsaWRhdGlvblNlY3VyZVNlcnZl
ckNBMi5jcmwwgYgGCCsGAQUFBwEBBHwwejBRBggrBgEFBQcwAoZFaHR0cDovL2Ny
dC5jb21vZG9jYTQuY29tL0NPTU9ET0VDQ0RvbWFpblZhbGlkYXRpb25TZWN1cmVT
ZXJ2ZXJDQTIuY3J0MCUGCCsGAQUFBzABhhlodHRwOi8vb2NzcC5jb21vZG9jYTQu
Y29tMIIDqAYDVR0RBIIDnzCCA5uCG3NuaTEzNzAwMy5jbG91ZGZsYXJlc3NsLmNv
bYISKi5iZWxhamFyYmFoYXNhLnVzggwqLmJ1Y2hiZWUuY2aCDiouYnVjaG1ha2Vy
LmNmghAqLmJ1cm5lb29vbzc3Lm1sghQqLmNsb3Roc2hvZXNwcHRqLmNvbYIMKi5k
aWxsbm90LmNmghEqLmV0aGl4ZGVzaWduLmNvbYISKi5ldXJvLW5hdXRpY2EuY29t
ghwqLmdkdGJvZHl0cmFuc2Zvcm1hdGlvbnMuY29tghAqLmdlcmFyZG5pY28uY29t
ggwqLmdzZzM5NS5jb22CDCouZ3N6NzE1LmNvbYITKi5pcGlja3lvdXJtZWRpYS5j
ZoIMKi5pdHMtMzY1LnJ1gg8qLm5pcmFsbW92aWUubWyCEioub3JnYW5pY2FyZ2Fu
Lm5ldIITKi5wYXVsbWVlaGFuYXJ0LmNvbYILKi5wbHJwZGYuZ3GCESoucHV5ZW5n
LmRvd25sb2FkghAqLnJlYWwtZm9vZHMubmV0ggwqLnJpYm9ueS5vcmeCCyouc2pi
b29rLmdxgg8qLnN0YXJlcGxheS5jb22CESouc3VnZ2VzdC11cmwub3JnghEqLnRh
aXdhbmZmYWlyLmNvbYIMKi50b2xnYXkueHl6gg4qLnR3dHRlbXB0LmNvbYIQYmVs
YWphcmJhaGFzYS51c4IKYnVjaGJlZS5jZoIMYnVjaG1ha2VyLmNmgg5idXJuZW9v
b283Ny5tbIISY2xvdGhzaG9lc3BwdGouY29tggpkaWxsbm90LmNmgg9ldGhpeGRl
c2lnbi5jb22CEGV1cm8tbmF1dGljYS5jb22CGmdkdGJvZHl0cmFuc2Zvcm1hdGlv
bnMuY29tgg5nZXJhcmRuaWNvLmNvbYIKZ3NnMzk1LmNvbYIKZ3N6NzE1LmNvbYIR
aXBpY2t5b3VybWVkaWEuY2aCCml0cy0zNjUucnWCDW5pcmFsbW92aWUubWyCEG9y
Z2FuaWNhcmdhbi5uZXSCEXBhdWxtZWVoYW5hcnQuY29tgglwbHJwZGYuZ3GCD3B1
eWVuZy5kb3dubG9hZIIOcmVhbC1mb29kcy5uZXSCCnJpYm9ueS5vcmeCCXNqYm9v
ay5ncYINc3RhcmVwbGF5LmNvbYIPc3VnZ2VzdC11cmwub3Jngg90YWl3YW5mZmFp
ci5jb22CCnRvbGdheS54eXqCDHR3dHRlbXB0LmNvbTAKBggqhkjOPQQDAgNJADBG
AiEAt0eJnUQu0fj55Jbq1dhjv7zmhJNsTEowx0ApbLFlpiQCIQCtJ5jyklj7Ic65
opXIMhs5N0wzGv7d38VJqSXgFJcWug==
-----END CERTIFICATE-----
1 s:/C=GB/ST=Greater Manchester/L=Salford/O=COMODO CA Limited/CN=COMODO ECC Domain Validation Secure Server CA 2
i:/C=GB/ST=Greater Manchester/L=Salford/O=COMODO CA Limited/CN=COMODO ECC Certification Authority
-----BEGIN CERTIFICATE-----
MIIDnzCCAyWgAwIBAgIQWyXOaQfEJlVm0zkMmalUrTAKBggqhkjOPQQDAzCBhTEL
MAkGA1UEBhMCR0IxGzAZBgNVBAgTEkdyZWF0ZXIgTWFuY2hlc3RlcjEQMA4GA1UE
BxMHU2FsZm9yZDEaMBgGA1UEChMRQ09NT0RPIENBIExpbWl0ZWQxKzApBgNVBAMT
IkNPTU9ETyBFQ0MgQ2VydGlmaWNhdGlvbiBBdXRob3JpdHkwHhcNMTQwOTI1MDAw
MDAwWhcNMjkwOTI0MjM1OTU5WjCBkjELMAkGA1UEBhMCR0IxGzAZBgNVBAgTEkdy
ZWF0ZXIgTWFuY2hlc3RlcjEQMA4GA1UEBxMHU2FsZm9yZDEaMBgGA1UEChMRQ09N
T0RPIENBIExpbWl0ZWQxODA2BgNVBAMTL0NPTU9ETyBFQ0MgRG9tYWluIFZhbGlk
YXRpb24gU2VjdXJlIFNlcnZlciBDQSAyMFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcD
QgAEAjgZgTrJaYRwWQKOqIofMN+83gP8eR06JSxrQSEYgur5PkrkM8wSzypD/A7y
ZADA4SVQgiTNtkk4DyVHkUikraOCAWYwggFiMB8GA1UdIwQYMBaAFHVxpxlIGbyd
nepBR9+UxEh3mdN5MB0GA1UdDgQWBBRACWFn8LyDcU/eEggsb9TUK3Y9ljAOBgNV
HQ8BAf8EBAMCAYYwEgYDVR0TAQH/BAgwBgEB/wIBADAdBgNVHSUEFjAUBggrBgEF
BQcDAQYIKwYBBQUHAwIwGwYDVR0gBBQwEjAGBgRVHSAAMAgGBmeBDAECATBMBgNV
HR8ERTBDMEGgP6A9hjtodHRwOi8vY3JsLmNvbW9kb2NhLmNvbS9DT01PRE9FQ0ND
ZXJ0aWZpY2F0aW9uQXV0aG9yaXR5LmNybDByBggrBgEFBQcBAQRmMGQwOwYIKwYB
BQUHMAKGL2h0dHA6Ly9jcnQuY29tb2RvY2EuY29tL0NPTU9ET0VDQ0FkZFRydXN0
Q0EuY3J0MCUGCCsGAQUFBzABhhlodHRwOi8vb2NzcC5jb21vZG9jYTQuY29tMAoG
CCqGSM49BAMDA2gAMGUCMQCsaEclgBNPE1bAojcJl1pQxOfttGHLKIoKETKm4nHf
EQGJbwd6IGZrGNC5LkP3Um8CMBKFfI4TZpIEuppFCZRKMGHRSdxv6+ctyYnPHmp8
7IXOMCVZuoFwNLg0f+cB0eLLUg==
-----END CERTIFICATE-----
2 s:/C=GB/ST=Greater Manchester/L=Salford/O=COMODO CA Limited/CN=COMODO ECC Certification Authority
i:/C=SE/O=AddTrust AB/OU=AddTrust External TTP Network/CN=AddTrust External CA Root
-----BEGIN CERTIFICATE-----
MIID0DCCArigAwIBAgIQQ1ICP/qokB8Tn+P05cFETjANBgkqhkiG9w0BAQwFADBv
MQswCQYDVQQGEwJTRTEUMBIGA1UEChMLQWRkVHJ1c3QgQUIxJjAkBgNVBAsTHUFk
ZFRydXN0IEV4dGVybmFsIFRUUCBOZXR3b3JrMSIwIAYDVQQDExlBZGRUcnVzdCBF
eHRlcm5hbCBDQSBSb290MB4XDTAwMDUzMDEwNDgzOFoXDTIwMDUzMDEwNDgzOFow
gYUxCzAJBgNVBAYTAkdCMRswGQYDVQQIExJHcmVhdGVyIE1hbmNoZXN0ZXIxEDAO
BgNVBAcTB1NhbGZvcmQxGjAYBgNVBAoTEUNPTU9ETyBDQSBMaW1pdGVkMSswKQYD
VQQDEyJDT01PRE8gRUNDIENlcnRpZmljYXRpb24gQXV0aG9yaXR5MHYwEAYHKoZI
zj0CAQYFK4EEACIDYgAEA0d7L3XJghWF+3XkkRbUq2KZ9T5SCwbOQQB/l+EKJDwd
AQTuPdKNCZcM4HXk+vt3iir1A2BLNosWIxatCXH0SvQoULT+iBxuP2wvLwlZW6Vb
CzOZ4sM9iflqLO+y0wbpo4H+MIH7MB8GA1UdIwQYMBaAFK29mHo0tCb3+sQmVO8D
veAky1QaMB0GA1UdDgQWBBR1cacZSBm8nZ3qQUfflMRId5nTeTAOBgNVHQ8BAf8E
BAMCAYYwDwYDVR0TAQH/BAUwAwEB/zARBgNVHSAECjAIMAYGBFUdIAAwSQYDVR0f
BEIwQDA+oDygOoY4aHR0cDovL2NybC50cnVzdC1wcm92aWRlci5jb20vQWRkVHJ1
c3RFeHRlcm5hbENBUm9vdC5jcmwwOgYIKwYBBQUHAQEELjAsMCoGCCsGAQUFBzAB
hh5odHRwOi8vb2NzcC50cnVzdC1wcm92aWRlci5jb20wDQYJKoZIhvcNAQEMBQAD
ggEBAB3H+i5AtlwFSw+8VTYBWOBTBT1k+6zZpTi4pyE7r5VbvkjI00PUIWxB7Qkt
nHMAcZyuIXN+/46NuY5YkI78jG12yAA6nyCmLX3MF/3NmJYyCRrJZfwE67SaCnjl
lztSjxLCdJcBns/hbWjYk7mcJPuWJ0gBnOqUP3CYQbNzUTcp6PYBerknuCRR2RFo
1KaFpzanpZa6gPim/a5thCCuNXZzQg+HCezF3OeTAyIal+6ailFhp5cmHunudVEI
kAWvL54TnJM/ev/m6+loeYyv4Lb67psSE/5FjNJ80zXrIRKT/mZ1JioVhCb3ZsnL
jbsJQdQYr7GzEPUQyp2aDrV1aug=
-----END CERTIFICATE-----
---
- Server certificate
Server certificate
subject=/OU=Domain Control Validated/OU=PositiveSSL Multi-Domain/CN=sni137003.cloudflaressl.com
issuer=/C=GB/ST=Greater Manchester/L=Salford/O=COMODO CA Limited/CN=COMODO ECC Domain Validation Secure Server CA 2
---
- Client certificate
No client certificate CA names sent
Peer signing digest: SHA256
Server Temp Key: ECDH, P-256, 256 bits
---
- handshake
SSL handshake has read 4298 bytes and written 467 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-ECDSA-AES128-GCM-SHA256
Server public key is 256 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-ECDSA-AES128-GCM-SHA256
Session-ID: C03826B6371333E99FF0A681A4E83C1EA22843B87ED884D14FB9896ADCA5C59D
Session-ID-ctx:
Master-Key: B68EE858A2B550BCA4CB9AC3E9EE37C20458033573D94F93556FA27E4E59090C50F35F25835527BBD265FB49A15F6669
Key-Arg : None
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 64800 (seconds)
TLS session ticket:
0000 - 85 f1 17 c7 b0 5e 0b 66-34 78 48 38 94 56 90 f8 .....^.f4xH8.V..
0010 - bd 97 75 98 6e 48 14 57-33 9b 78 20 9e 2c 5d 34 ..u.nH.W3.x .,]4
0020 - 45 c7 c7 0e d2 31 c2 c3-58 7b 75 a9 66 2a 94 1b E....1..X{u.f*..
0030 - 44 32 0d a0 ec dd b4 9f-f3 17 61 ff fc 33 81 8b D2........a..3..
0040 - 84 22 37 94 43 d7 3f fd-10 7c aa e7 8b b9 fc 9a ."7.C.?..|......
0050 - 49 b6 a9 50 9d 8c 92 c6-63 e2 e4 c8 cc 53 b2 cf I..P....c....S..
0060 - 1b b9 fb 15 b4 59 f7 d0-7b c8 b0 77 8f 2e 0a c0 .....Y..{..w....
0070 - 90 77 6b 05 a1 8a b1 b7-da 34 ce 0c 51 be 64 f6 .wk......4..Q.d.
0080 - 12 8c 4c 57 17 08 4f 5a-c3 67 99 82 c3 94 b7 f0 ..LW..OZ.g......
0090 - 29 50 f1 d6 c5 9a a2 59-a0 99 90 26 14 a3 6f bf )P.....Y...&..o.
00a0 - 1c bc 87 39 ba 75 4f 44-a5 9c ab a8 2c ad 3e 84 ...9.uOD....,.>.
Start Time: 1517815405
Timeout : 300 (sec)
Verify return code: 0 (ok)
---
Chrome devtool
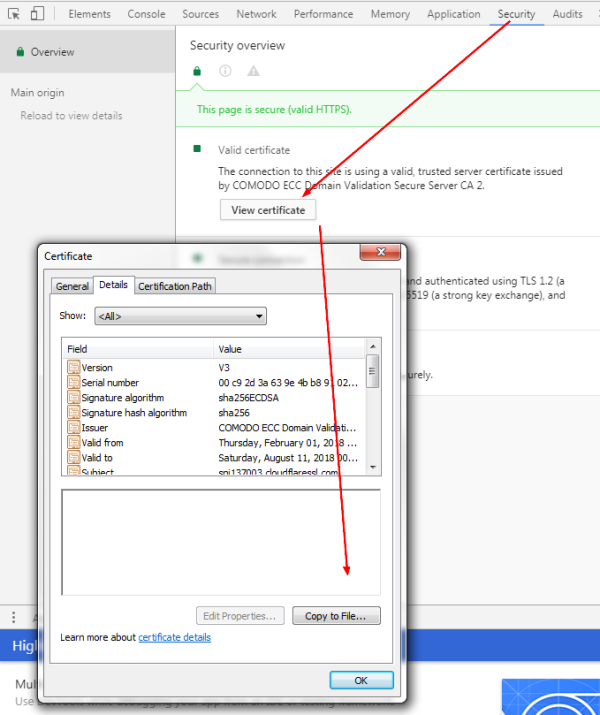
Firefox
Export certificate from Firefox Browser
- more info“ > “security” > “show certificate” > “details” > “export..
Local
openssl local decryption
You may have a certificate in its coded form (pem), to read the details of the certificate just issue the following command:
openssl x509 -in newcert.pem -noout -text
Certificate:
Data:
Version: 1 (0x0)
Serial Number:
9f:97:73:c5:0e:6f:00:08
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=NL, ST=Noord-holland, L=Oegstgeest, O=GerardNico, OU=Nerdy, CN=Nico/[email protected]
Validity
Not Before: Feb 12 22:03:53 2018 GMT
Not After : Feb 12 22:03:53 2019 GMT
Subject: C=NL, ST=Noord-holland, L=Oegstgeest, O=GerardNico, OU=Nerdy, CN=Nico/[email protected]
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (1024 bit)
Modulus:
00:c0:42:e3:1f:ac:4a:d8:cc:f6:fe:0d:0a:ba:3f:
dd:28:f1:6c:d3:5d:3e:e0:90:63:fa:d4:de:dc:1b:
49:1a:f4:be:22:d1:6b:35:e2:97:7a:b7:cd:b4:b2:
be:5d:e9:87:8a:52:05:f1:99:3e:4d:18:be:e6:1e:
45:0a:bb:96:75:90:59:31:e8:28:ca:f4:b3:05:c9:
64:23:90:4e:a1:c6:77:5c:71:a9:9b:5c:72:67:dc:
71:61:7f:6b:3d:b6:e0:a1:50:21:13:da:db:47:94:
ad:8e:72:f0:97:40:d2:2e:6a:22:4a:88:46:cc:0c:
8d:5d:b6:5c:f8:0b:dc:0e:39
Exponent: 65537 (0x10001)
Signature Algorithm: sha256WithRSAEncryption
40:0f:cc:9d:d6:b4:40:c7:e4:02:0d:44:ea:aa:0a:a6:b7:cb:
aa:8a:76:4b:b2:d4:82:43:4b:29:80:bc:0b:90:f0:88:87:6f:
bf:47:0c:52:7a:98:a5:e2:94:1e:7c:9b:19:83:78:c9:95:1b:
19:b5:d6:63:1c:f4:11:a9:04:b3:b1:10:a5:81:dd:f9:50:c8:
19:f2:45:f5:21:5c:d0:74:2a:94:6e:83:9e:a6:7d:3b:32:c0:
cf:b1:77:5c:ca:44:0f:96:c8:b4:43:6e:91:f8:35:31:e6:7a:
28:35:d8:32:17:89:42:b3:e2:b9:f1:e6:02:54:47:db:b7:ff:
a7:ab
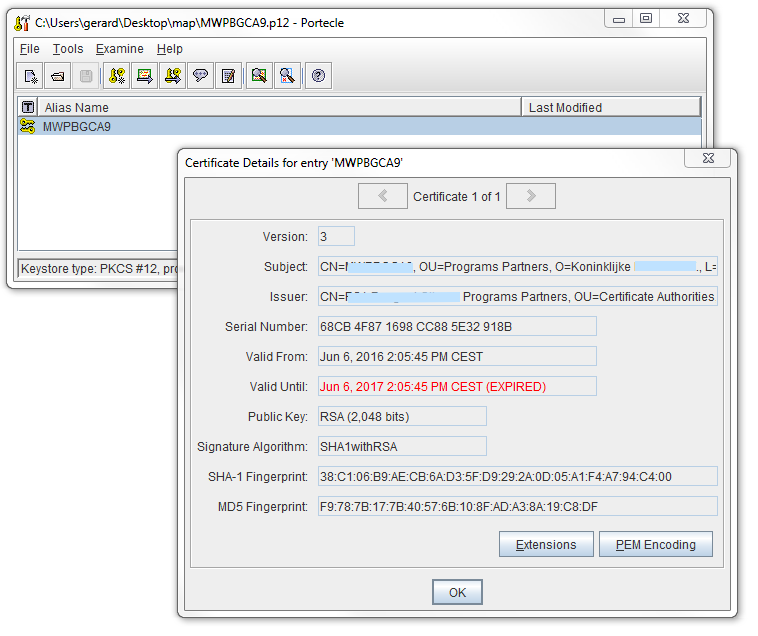
portecle
With Portecle, you can examine a certificate:
- by opening a keystore and double-clicking on it
- or via Examine > Examine Certificate (for a local file)
- or via Examine > Examine SSL/TLS certificate (for a server certificate)