Domain Validated Certificates (DV)
About
Domain Validated certificates are server signed certificates where the ownership of the domain was checked.
There is no identifying organizational information for these certificates and thus should never be used for commercial purposes.
It is the cheapest type of certificate to get.
This is the certificate used for public website.
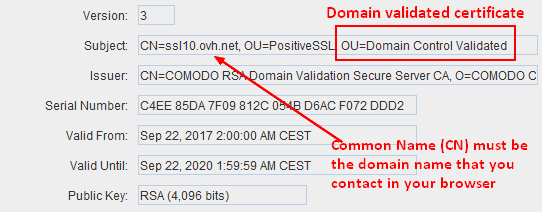
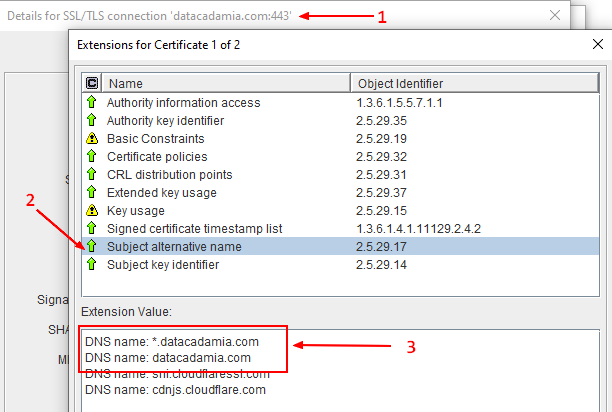
The full qualified domain name (DNS name) should match one of the following certificate property:
- the Common Name
Domain-validated certificates are based on proof of ownership of a domain, and is driven by a protocol called ACME
Security
Note that the Visitors to a website with Domain Validated (DV) certificates cannot validate, via the certificate, if the business on the site is legitimate.
Challenge
The ownership of a domain is checked via a challenge:
- setting a DNS TXT record with some value in the domain registry
- or hosting a file somewhere on a random path on the web site.
Lifetime
The maximum lifetime is 825 days (roughly 27 months) 3)
Example
Example (when the certificate is open with portecle)
- match the CN
- match via the Subject Alternative Name
Creation
This is an example of domain validated server certificate creation with openssl
The server.ini configuration file below set:
- the extendedKeyUsage to serverAuth to advertise that a server certificate must be created
- the keyUsage that goes with a serverAuth.
- the CN of the server (ie req_distinguished_name)
- explicitly that this is not a CA certificate with the basicConstraints
- the subject alternative name with a DNS name via the subjectAltName property that should match the DNS of the web server
[ req ]
# Options for the `req` tool: PKCS#10 certificate request and certificate generating utility. (`man req`)
distinguished_name = req_distinguished_name
# does not prompt for dn fields
prompt = no
# Default md (message digest to use for the hash/fingerprint)
# option: SHA-1 is deprecated, so use SHA-2 family instead
# TLS server certificates and issuing CAs must use a hash algorithm from the SHA-2 family in the signature algorithm
# https://support.apple.com/en-us/HT210176
default_md = sha256
[ req_distinguished_name ]
# CN used to create the CA server
C = Country
O = Organisation
CN = ServerName or DNS name
[ server_extensions ]
# List of extensions to add to certificate generated
# A CA certificate must contains: CA: true
basicConstraints = critical, CA:false
# Key Usage
keyUsage = critical, digitalSignature, keyAgreement, keyEncipherment
# Used for server auth
extendedKeyUsage=serverAuth
# as seen https://www.openssl.org/docs/man1.0.2/man1/openssl-req.html under v3_ca example
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid:always,issuer:always
subjectAltName=DNS:example.com,DNS:*.example.com
Then the OpenSSL command:
- Creation of the private key and certificate request
openssl req \
-new `# Ask a certificate signing request`\
-keyout server_private_key.pem `# The private key output (created if the key option is not given)` \
-nodes `#don't encrypt the created private key` \
-out server_csr.pem `# The certificate signing request (CSR) file ` \
-config server.ini
- Signing of the request with a CA certificate
openssl \
x509 `# output a certificate` \
-req `#input is a certificate request, sign and output` \
-days 365 `#How long till expiry of a signed certificate ` \
-in server_csr.pem \
-out server_certificate.pem \
-CA ca_certificate.pem \
-CAkey ca_private_key.pem \
-set_serial 0x"$(openssl rand -hex 16)" `# large random unique identifier for the certificate. ` \
-extensions server_extensions \
-extfile server.ini