About
This article show how to configure Weblogic in order to let OBIEE authenticate against Active Directory.
Once the AD domain is recognise as a valid user store to authenticate Oracle BI, users will be able to log in to Oracle BI EE using the same credentials as they use to log in to the Windows domain
Articles Related
Architecture
Each security realm must have at least one Authentication provider configured.
The WebLogic Security Framework supports multiple Authentication providers (and thus multiple LoginModules) for multipart authentication (since version 11.5). Therefore, you can use multiple Authentication providers as well as multiple types of Authentication providers in a security realm. Authentication providers are called in the order in which they were configured in the security realm.
When a user is authenticated into WebLogic Server, an authentication provider creates a Weblogic - Login Module (Control Flag and authentication flow) with a set of user and group principals, which include the user and group names, respectively. The LDAP Authentication providers included in WebLogic Server also store the guid and LDAP distinguished name (DN) data of users and groups as attributes of those principals.
See Weblogic - Login Module (Control Flag and authentication flow)
Prerequisites
In the Oracle BI Administration Tool, the user used for the Ldap - Configuration Parameters in the LDAP Server section must have both ldap_bind and ldap_search authority.
BI Configuration
The steps in this document have been tested with the following configuration
OBIEE 11:
- Oracle BI EE version 11.1.1.7.0 (Build 130303.2025 64-bit)
- and Active Directory 2008 (Windows Server 2008).
This document will not work with OBIEE 11g (11.1.1.3) because it does not support chaining of authenticators
OBIEE 12:
- OBIEE
Steps
Adding the Active Directory Authentication Provider
- Security Realm > Providers
- Lock and Edit
- New
- Name ADAuthenticator and type ActiveDirectoryAuthenticator
- Change the Weblogic - Login Module (Control Flag and authentication flow) of the authentication provider from REQUIRED to SUFFICIENT
- Reorder the providers and set in first position the Weblogic DefaultAuthenticator and set its control flag to SUFFICIENT. This is needed when the provider contains the BISystemUSer. The BI System account must be in the primary authentication module. ?
Set the critical node to false. Otherwise you may get this behaviour. See OBIEE 11g: Error: “Unable to Sign In An error occurred during authentication.” When You Try to Log in and One of Multiple Authentication Providers is Down
LDAP Parameters
You can see the value of the LDAP attribute by using a LDAP client. For instance, with Jexplorer
Ldap server
- Active Directory Server name/port
- Principal: the user that will query the LDAP server. The user doesn't need be an administrative account, but it does need to have sufficient privileges to be able to make arbitrary queries on the LDAP tree
- Password for Principal
User
- Base DN for the user. The DN (ie the node in the LDAP tree) where the search will start
- The setting of the user attribute as influence on others attributes. You need to set them as below:
| Attribute Name | Required Setting |
|---|---|
| UserNameAttribute | AUserAttribute |
| AllUsersFilter | (&(AUserAttribute =*)(objectclass=person)) |
| UserFromNameFilter | (&(AnOtherUserAttribute =%u)(objectclass=person)) |
where the AUserAttribute is for Active Directory:
- cn default (for an ldap server)
- sAMAccountName because it is the logon name used to support clients and servers running earlier versions of the operating system, such as Windows NT 4.0, Windows 95, Windows 98, and LAN Manager.
- mail … Doc
- userPrincipalName
Group
For the Groups
- Base DN: The node in the LDAP tree where the search will begin
- The group name influence others parameters. By default AnAttribute is cn but if you choose an other, it must be reflected in the below other parameters.
| Attribute Name | Value |
|---|---|
| Static Group Name Attribute | AnAttribute |
| AllGroupsFilter | (&(AnAttribute=*)(objectclass=group)) |
| GroupFromNameFilter | (&(AnAttribute=%g)(objectclass=group)) |
- Static Group Object Class: group
- Static Member DN Attribute: member (The attribute of a static LDAP group object that specifies the distinguished names (DNs) of the members of the group)
General
- GUID Attribute: objectguid for Active Directory
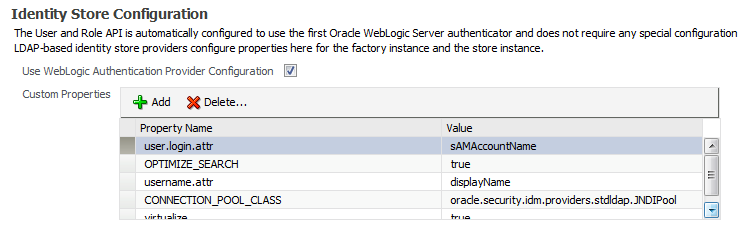
Identity Store configuration
Identity Store settings are reached via the Security Provider Configuration screen, which is accessed via Enterprise Manager. Select Weblogic Domain → bifoundation_domain→(right click) Security → Security Provider Configuration
Virtualization
virtualize true
This property can be either true (multi-LDAP lookup) or false (single-LDAP lookup). The default is false.
Verification:
$MY_DOMAIN=bi # in 12c
grep -n virtualize $FMW_HOME/user_projects/domains/$MY_DOMAIN/config/fmwconfig/jps-config.xml
<serviceInstance name="idstore.ldap" provider="idstore.ldap.provider">
<description>LDAP Identity Store Service Instance</description>
<property name="virtualize" value="true"/>
<property name="idstore.config.provider" value="oracle.security.jps.wls.internal.idstore.WlsLdapIdStoreConfigProvider"/>
<property name="CONNECTION_POOL_CLASS" value="oracle.security.idm.providers.stdldap.JNDIPool"/>
</serviceInstance>
Optimize_Search
OPTIMIZE_SEARCH must be set to true
Other
This configuration are only needed for older version. check with your documentation.
BISystemUser
Oracle Business Intelligence uses a specific user for the configured authentication provider for internal communication, you can create a new user in the external LDAP or use the pre-existing user in the Weblogic.
Identity Store configuration - User Attribute
No more needed from 11.7
For UserName Attribute only, you also need to add two properties to the Identity Store configuration (user.login.attr and and username.attr) to tell it about the attribute you’re expecting to get user name from (it defaults to using “uid” if none is specified).
user.login.attr sAMAccountName
username.attr displayName
Reboot and test
- Reboot the system
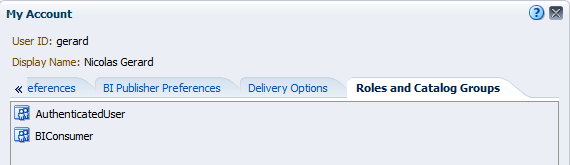
- You must be able to see all user and group in Console > Security Realm > myRealm > User and Group
- Then go to Presentation Services and try to login with a user. It will get automatically the BIConsumer application role because this role includes all authenticated user.
Support
[OBI-SEC-00101] System user validation failed
The system user profile could not be found in the identity store
You can find this error in a lot of log. Example:
- Weblogic Server Log
System user validation failed - the system user profile could not be found in the identity store.
oracle.bi.security.service.UserProfileNotFoundException
Unable to initialize oracle.bi.security.service.SecurityServiceBean
- BI Server log (NQServer.log)
[2014-07-07T13:41:41.000+02:00] [OracleBIServerComponent] [ERROR:1] [] [] [ecid: 004zPZpJz5EFO9WFLzrI8A0007V3000000] [tid: 6f893700] An error message was received from the BI Security Service: oracle.bi.security.service.SecurityServiceException: SecurityService::validateSystemUserProfile [OBI-SEC-00101] System user validation failed - the system user profile could not be found in the identity store.
[2014-07-07T13:41:41.000+02:00] [OracleBIServerComponent] [ERROR:1] [] [] [ecid: 004zPZpJz5EFO9WFLzrI8A0007V3000000] [tid: 6f893700] [13026] Error in getting roles from BI Security Service: 'An error message was received from the BI Security Service: oracle.bi.security.service.SecurityServiceException: SecurityService::validateSystemUserProfile [OBI-SEC-00101] System user validation failed - the system user profile could not be found in the identity store.'
When adding a new LDAP provider, Weblogic expects to see the bisystemuser in the first provider. It must also return the result directly and therefore must be flagged with the SUFFICIENT control flag ???