About
Secure Shell or SSH is a application protocol that allows data to be exchanged using a secure channel between two networked devices.
Used primarily on GNU/Linux and Unix based systems to access shell accounts, SSH was designed as a replacement for Telnet and other insecure remote shells, which send information, notably passwords, in plaintext, rendering them susceptible to packet analysis. The encryption used by SSH provides confidentiality and integrity of data over an insecure network, such as the Internet.
Architecture
The SSH protocol consists of three major components:
- The User Authentication Protocol authenticates the client to the server.
- The Connection Protocol multiplexes the encrypted tunnel into several logical channels.
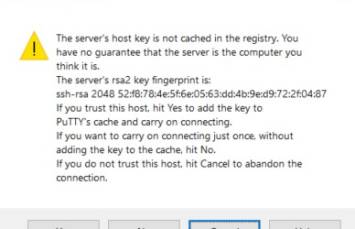
Host Key
Each server host SHOULD have a host key. The server host key is used during key exchange to verify that the client is really talking to the correct server.
Starting a shell or a command
Once the session has been set up, a program is started at the remote end.
The program can be:
- a shell (shell),
- an application program (exec), (The server SHOULD NOT halt the execution of the protocol stack when starting a shell or a program. All input and output from these SHOULD be redirected to the channel or to the encrypted tunnel.)
- or a subsystem with a host-independent name (subsystem). (It will execute a predefined subsystem. It is expected that these will include a general file transfer mechanism, and possibly other features.)
Only one of these requests can succeed per channel.
Service Request
After the key exchange, the client requests a service. The service is identified by a name.
- ssh-userauth
- ssh-connection
If the server supports the service (and permits the client to use it), it must accept it.
Config
Specification
The SSH specification is the following set of specification:
Documentation / Reference
- Library Implementation: