What is a Network Communication Protocol?
About
A network protocol is a protocol:
- that describes the computer language
- that will allow two or more computer processes to communicate together.
Protocols are instructions for multiple agents. Algorithms are instructions for single agents.
Level
A protocol has only one OSI level (Open Systems Interconnection)
Lower Level
These Protocols are in the lower Layer level of OSI (Open Systems Interconnection) and manipulate packets.
They implement packets:
- Addressing,
- routing
- and traffic control
Example: The most known are the protocols in the Transport layer
These protocols communicate via sockets
| Type | Client Server Installation Machine |
|---|---|
| TCP/IP sockets | Two different |
| UNIX domain sockets | Same |
| Shared Memory | Same |
Using a Shared Memory segment allows for the best performance, but greater memory usage. Using UNIX domain sockets allows for improved performance over TCP/IP, but with less memory consumption than a shared memory segment connection.
Higher level
This higher level (mostly the Application Layer (level 7)) is a wrapper around the lower levels and exposes you with a message (and not with packet)
Example:
Web:
- What is SMTP?: Mail
Console
IP
Message
Naming directory
- LDAP: Directory
Banner
The banner is the first message that the server sends before any protocol exchange when a client connects.
Visualisation
A protocol being a process between multiple agents is visualized with all process diagrams such as:
Example of Sequence for the oauth code flow
Operating System
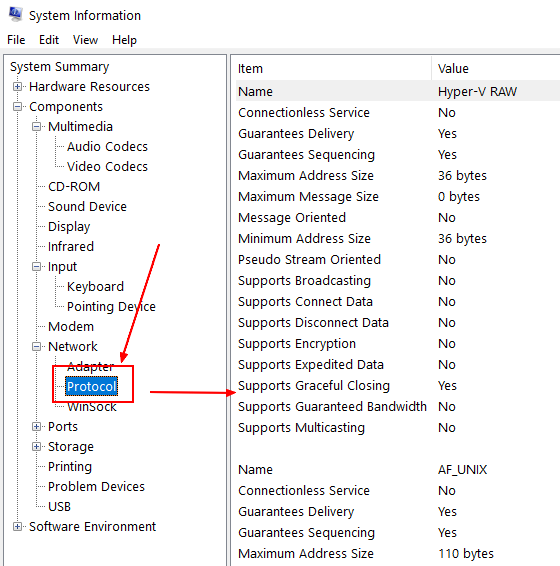
Windows
Windows - System Information will list low network protocol (OSI Layer 4) such as:
- bluetooth